Sentinel AK-XL: Building a Virtual SOC When Cybersecurity Training Meets Reality
Imagine walking into your first day as a SOC analyst, staring at walls of blinking monitors displaying alerts, dashboards, and threat intelligence feeds. The reality hits you: your textbook knowledge suddenly feels insufficient when facing real-time cyber threats targeting your organization.
That disconnect between academic cybersecurity education and practical SOC operations is exactly what inspired us to build Sentinel AK-XL - a comprehensive Virtual Security Operations Center that doesn't just teach theory, but provides hands-on experience with enterprise-grade security tools.
The Challenge with Traditional Cybersecurity Education
Most cybersecurity programs do an excellent job teaching concepts: threat modeling, incident response frameworks, security architectures. But there's often a significant gap when it comes to practical experience with the actual tools and workflows that SOC analysts use daily.
Students graduate knowing about SIEM platforms, threat detection, and incident response, but they've never actually:
Configured a real SIEM to collect and correlate security events
Built dashboards that security teams rely on for threat visibility
Investigated actual attack patterns or responded to live incidents
Worked with the enterprise security stack that powers modern SOCs
This gap became particularly apparent during our cybersecurity specialization program, where we needed to demonstrate not just theoretical knowledge, but practical proficiency in security operations.
Enter Sentinel AK-XL
Our solution was to build a production-grade Virtual SOC environment that could serve as both a capstone project and a training platform for future cybersecurity professionals.
Sentinel AK-XL isn't a toy or simulation - it's built using the same enterprise tools that power real Security Operations Centers:
ELK Stack 9.1.2 for log aggregation and visualization
Wazuh 4.12.0 as the SIEM detection engine
Docker containerization for scalable deployment
VirusTotal API integration for threat intelligence
Geographic IP enrichment for attack attribution
Sysmon for Windows endpoint monitoring
How We Built It
The project was a collaborative effort between three cybersecurity specialists, each bringing different expertise:
Abimael Pérez led the SOC dashboard development and operational documentation, ensuring our interfaces matched what analysts actually use in production environments.
Luis Soto focused on attack simulation and red team operations, creating realistic threat scenarios that would generate meaningful alerts and require actual investigation skills.
Xavier Cruz (that's me) handled the SOC architecture, infrastructure engineering, and deployment automation - making sure everything worked together seamlessly and could be deployed reliably.
Real Training, Real Experience
What makes Sentinel AK-XL special isn't just the technology stack - it's the realistic attack scenarios and comprehensive training workflows we've built around it.
The platform includes:
Attack Simulations: From SSH brute force attacks to network reconnaissance and malware detection scenarios, students face the same types of threats that SOC analysts deal with daily.
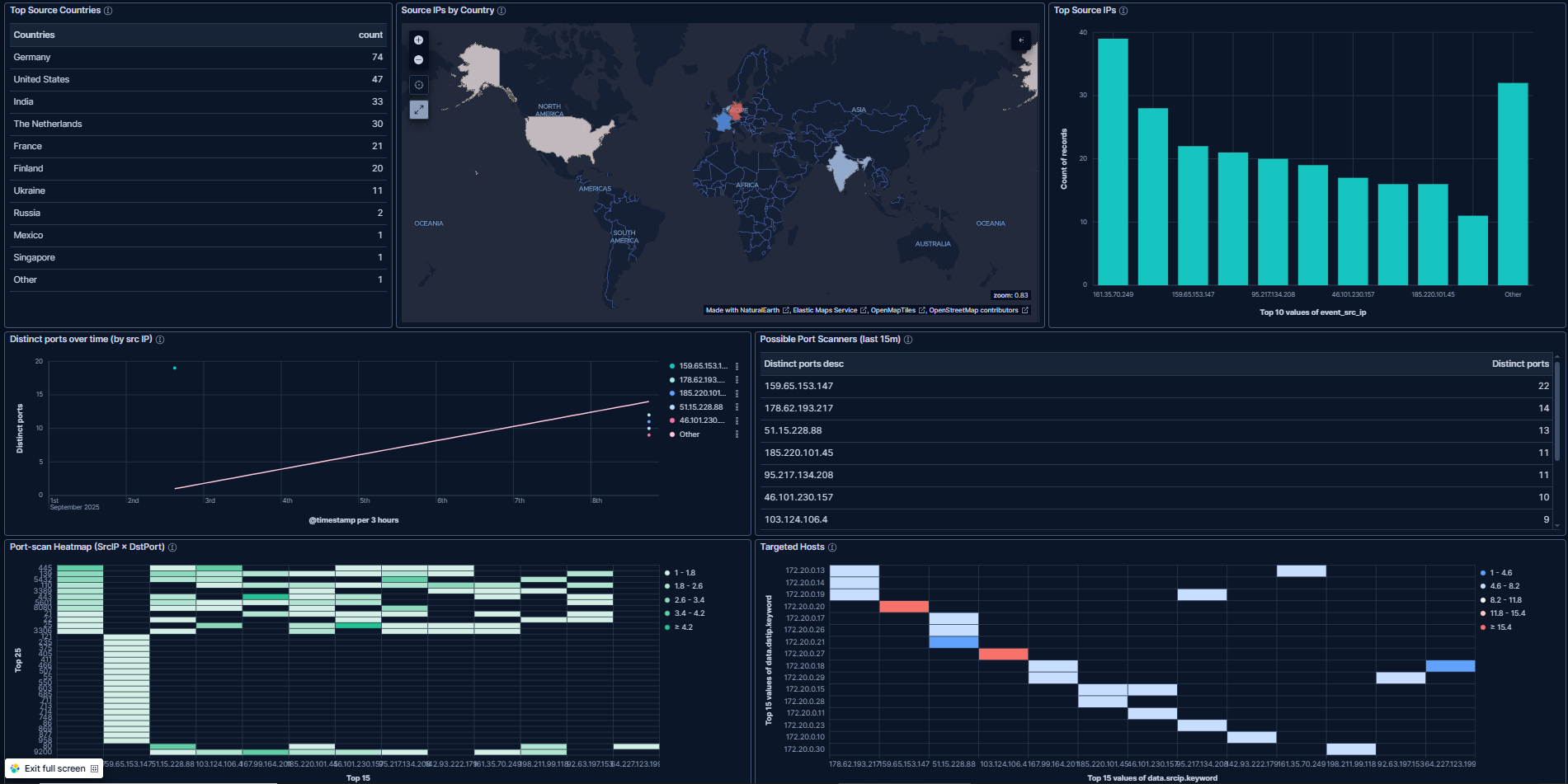
Professional Dashboards: Our five specialized dashboards provide real-time threat monitoring, authentication analysis, network traffic visualization, and threat intelligence correlation.
Analyst Playbooks: Step-by-step incident response procedures that guide students through proper investigation and documentation processes.
Geographic Threat Intelligence: Attack attribution and mapping capabilities that show students how global threat patterns emerge and evolve.
Beyond the Classroom
While Sentinel AK-XL was developed as our cybersecurity program capstone, its impact extends far beyond academic requirements. The platform demonstrates several important principles:
Hands-on Learning: Nothing replaces actual experience with security tools and real threat scenarios.
Industry Alignment: Training environments should mirror production systems as closely as possible.
Comprehensive Documentation: Professional security operations depend on clear procedures and knowledge transfer.
Collaborative Development: Complex security projects require diverse expertise and coordinated teamwork.
The Real-World Impact
The most rewarding aspect of this project has been seeing how it bridges the gap between academic cybersecurity education and professional security operations. Students using Sentinel AK-XL don't just learn about SOC operations - they actually perform them.
They configure SIEM rules, investigate suspicious network traffic, correlate threat intelligence, and respond to security incidents using the same tools and procedures they'll encounter in their careers.
Looking Forward
Cybersecurity threats continue evolving, and so must our training approaches. Sentinel AK-XL represents one step toward more practical, hands-on cybersecurity education that prepares students for the realities of modern security operations.
The platform is open source and designed to be extended with additional attack scenarios, enhanced detection capabilities, and integration with emerging security technologies.
Whether you're a cybersecurity student looking for practical experience, an educator seeking realistic training scenarios, or a security professional wanting to test new detection techniques, Sentinel AK-XL provides a comprehensive platform for hands-on security operations learning.
Because when it comes to cybersecurity, there's no substitute for real experience with real tools facing real threats.
Interested in exploring Sentinel AK-XL? Check out the project repository for complete documentation, installation guides, and training scenarios.